I believe Azure Private LInk is really essential feature especially for enterprise customers because this feature enables to exclusively expose your Azure PaaS resources and Azure VM resources. At first, we should confirm again that Azure Private Link has two types of features.
- private link service: Expose endpoints by using Standard Load Balancer. These endpoints will be used by "private endpoint"
- private endpoint: You can access Azure PaaS Services (for example, Azure Storage and SQL Database) and your endpoints exposed by "private link service" over a private endpoint in your virtual network.
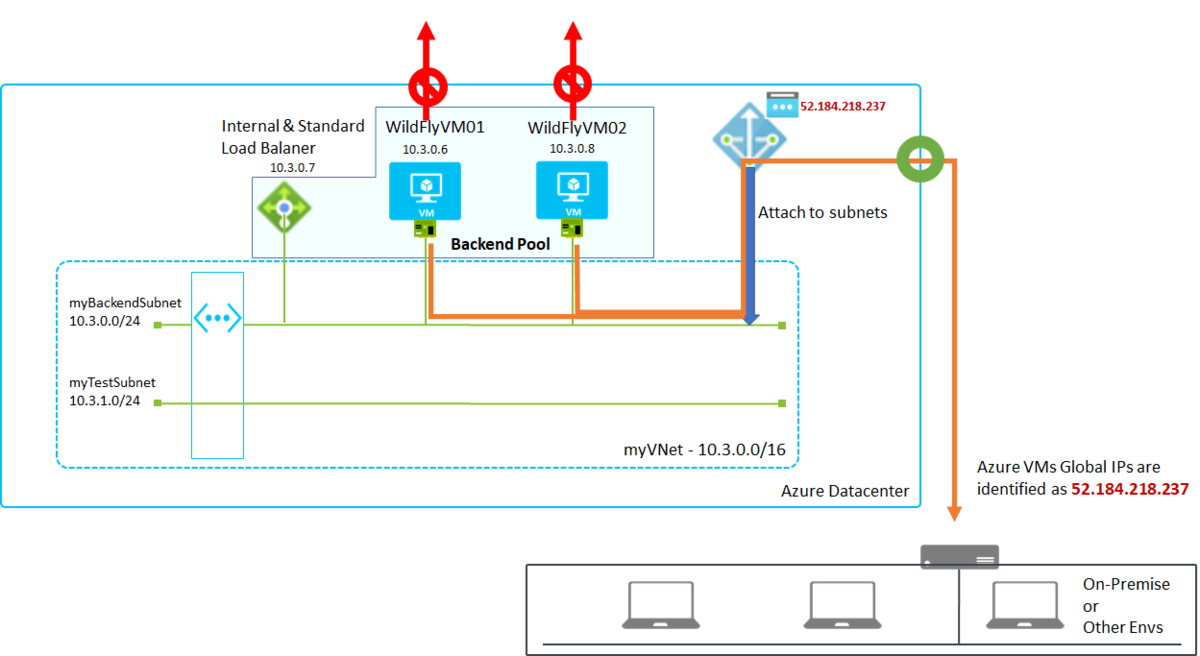
This is a simple architecture with Private Link. Private Link( Private Endpoint and Private Link Service) will create VNICs automatically into VNETs enabled Private Link like below.
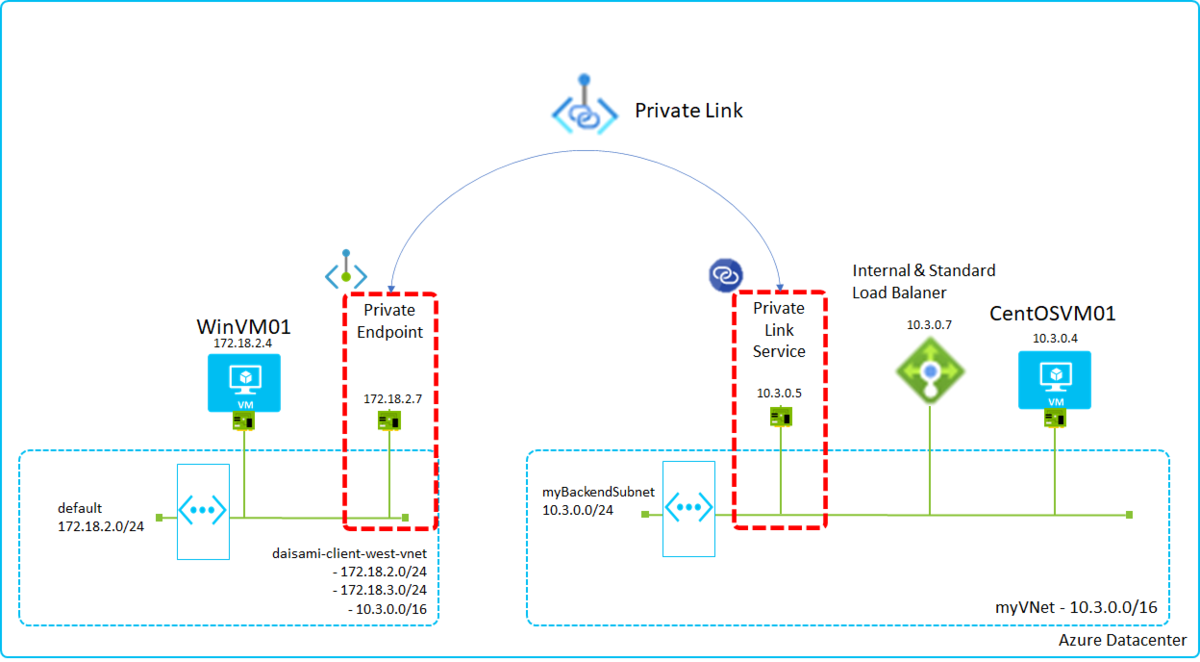
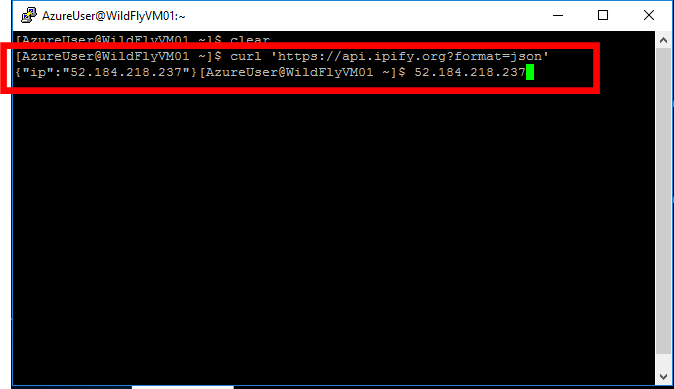
Azure resources communicate each others exclusively with the created NICs. In this image, CentOSVM01 on myVNet exposes its endpoints with SLB(Standard Load Balancer) and SLB privately exposes endpoints with Private Link Service, so WinVM01 can access CentOSVM01 by using Private Endpoint.
You can find IP address spaces are overlapped in both VNETs but it works well by using Private Link.
What's benefits?
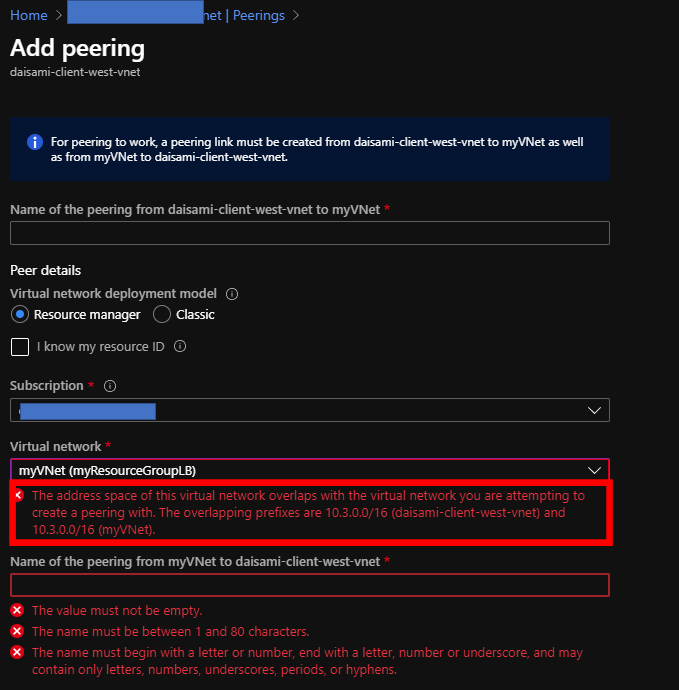
I believe one of the biggest benefits is you will no longer need to worry about IP addresses overlapping. VNET Peering is also quite useful feature but you have to always note addresses overlapping. You will get error messages below if you will try to connect overlapped VNETs.
Try "private link service"
You can create your "private link service" just following an article below. Please note to use "Standard Load Balancer". In addition that, you have to choose "Internal" Load Balancer to expose your endpoints exclusively.
Quickstart - Create a Private Link service by using the Azure portal | Microsoft Docs
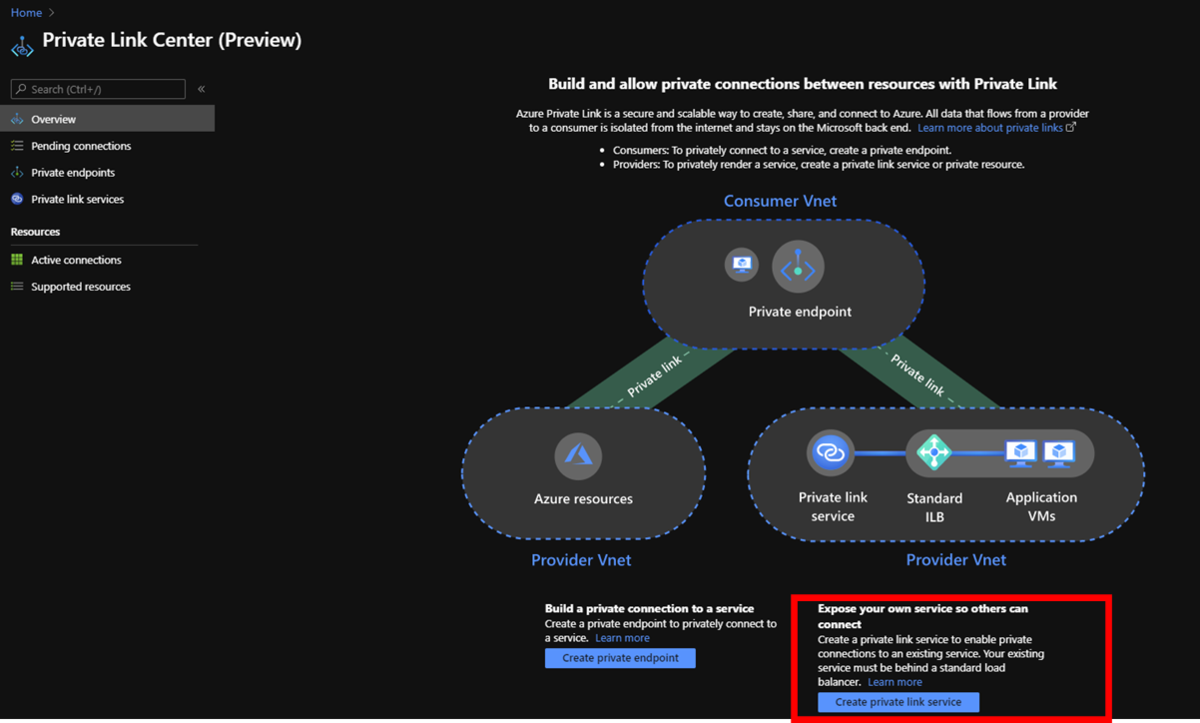
Go to Private Link Center page on Azure Portal and Click "Create private link service" below.
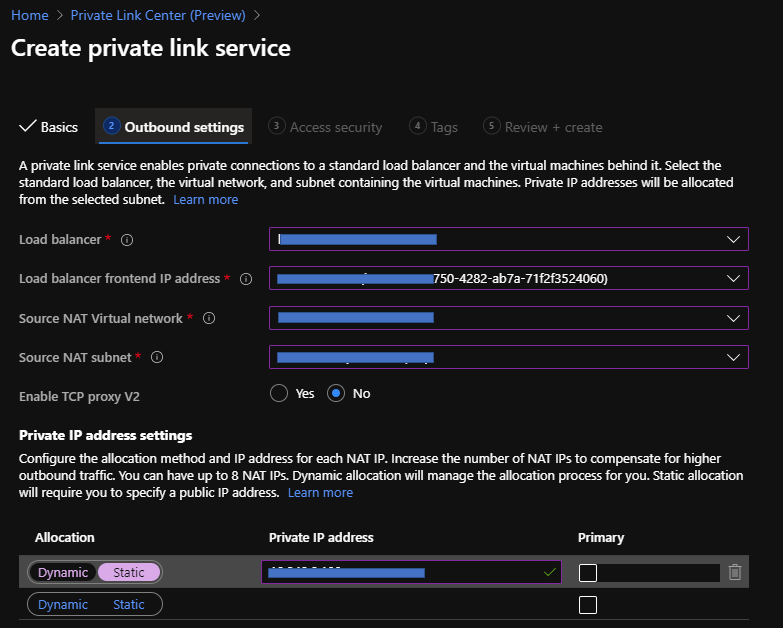
You can find only Standard Load from this menu and setup each items properly by following wizards.
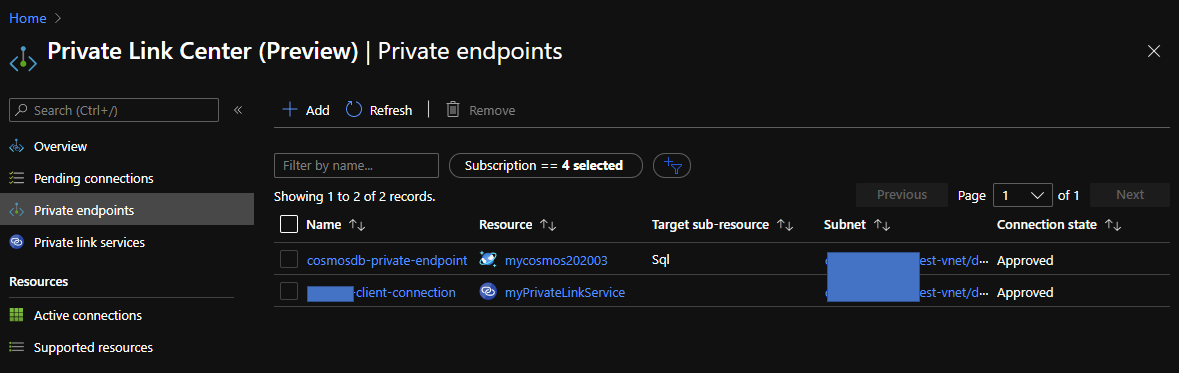
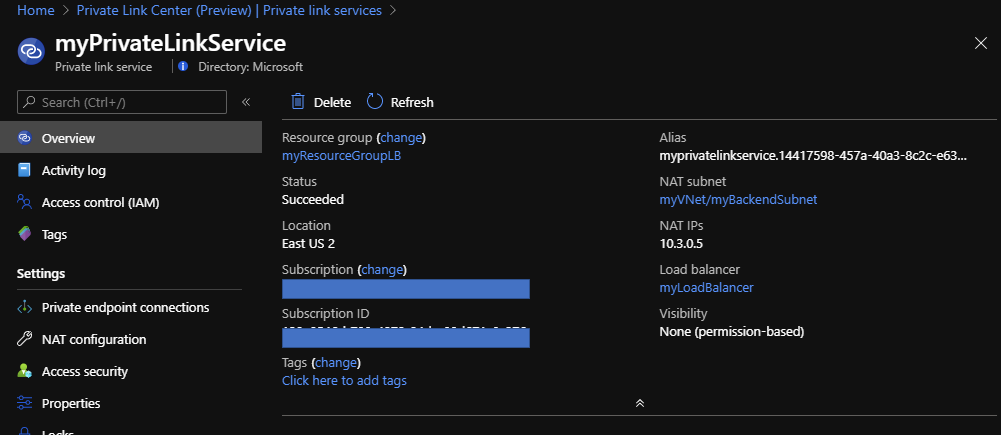
Finally, you can confirm the result like here.
Try "private endpoint"
It's easy to enable "private endpoint" for Azure PaaS features but we have to utilize command lines for your "private link service" endpoints. Here is sample and also refer to az network private-endpoint | Microsoft Docs.
az login
az account set -s "your subscription ID"
az network private-endpoint create \
--resource-group "resource group name having a vnet to connet your endpoints" \
--name "name of private endpoint" \
--vnet-name "vnet name to connet your endpoints" \
--subnet "subnet name of the vnet" \
--private-connection-resource-id "/subscriptions/your subscription name/resourceGroups/your resource group name/providers/Microsoft.Network/privateLinkServices/your endpointname"
--connection-name "Name of the private link service connection"\
--location "region ex. westus"
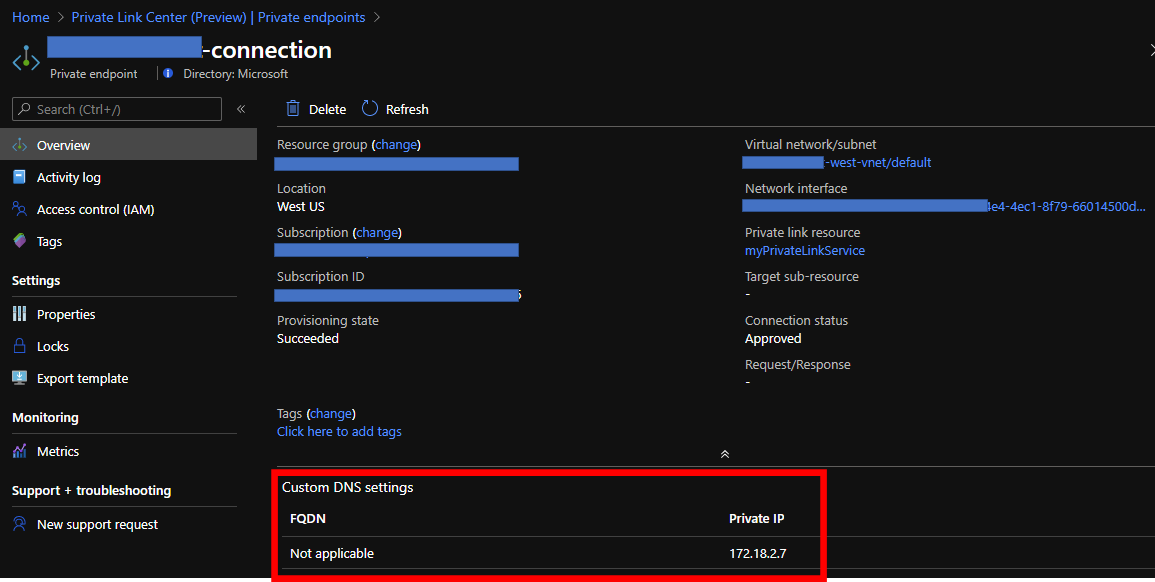
You can confirm your private endpoint like below if the command works well.