It was sometimes painful task to change settings, connection string and others depending on environment - production, QT, staging or development. It's also quite important to ensure to keep secret and security for others. As a solution for the case, you can significantly simplify to retrieve secrets from Azure Key Vault with Managed Identity even now. In this post, you can acquire knowledge how to completely separate settings and password from application codes by using App Service, Azure Key Vault and Managed Identity like below.
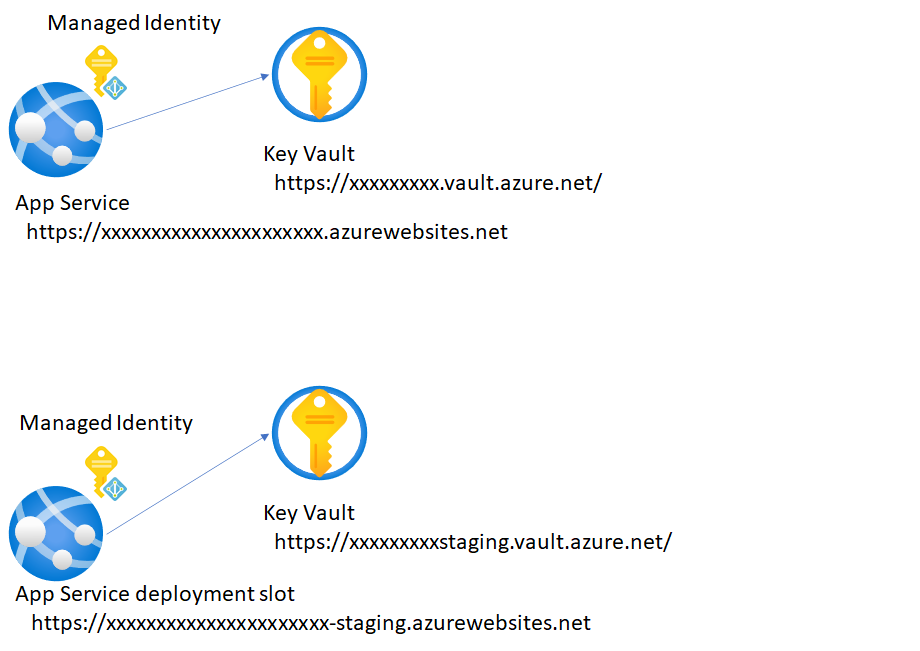
From next section, you can setup single environment by using App Service and Key Vault first,
App Service by using Managed Identity and Azure Key Vault
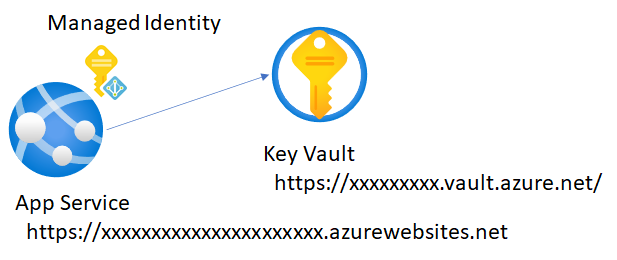
In this section, you need to reminder how to setup Managed Identity and Azure Key Vault on App Service with single environment. First, create your App Service and Key Vault like below.
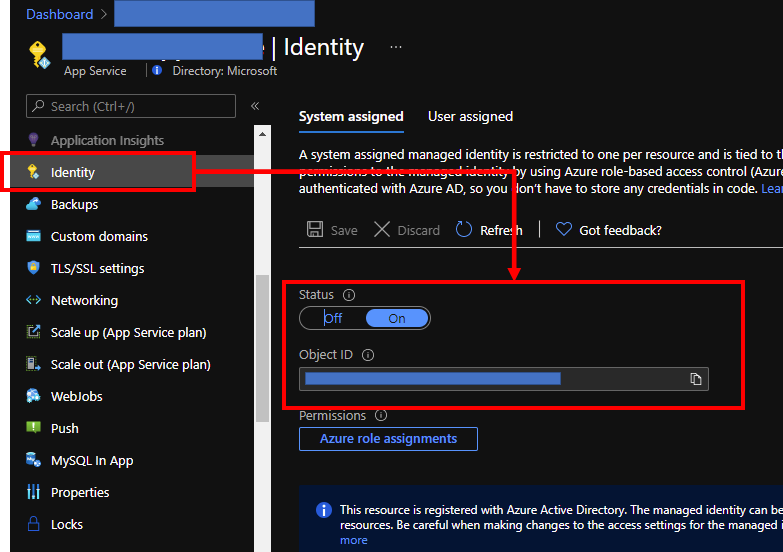
Enable System assigned managed identity like here. And pick up Object ID for this managed identity.
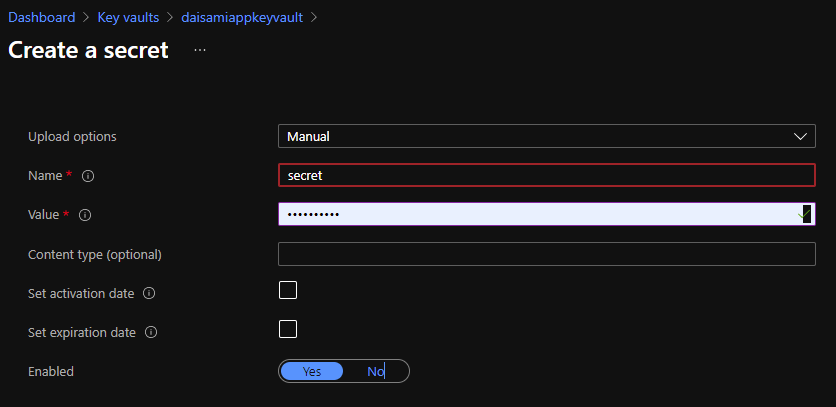
Visit your Key Vault and create "Secret" like here to retrieve from your apps on Azure App Service in later.
Assign access policy to your managed identity on Azure App Service by following steps below.
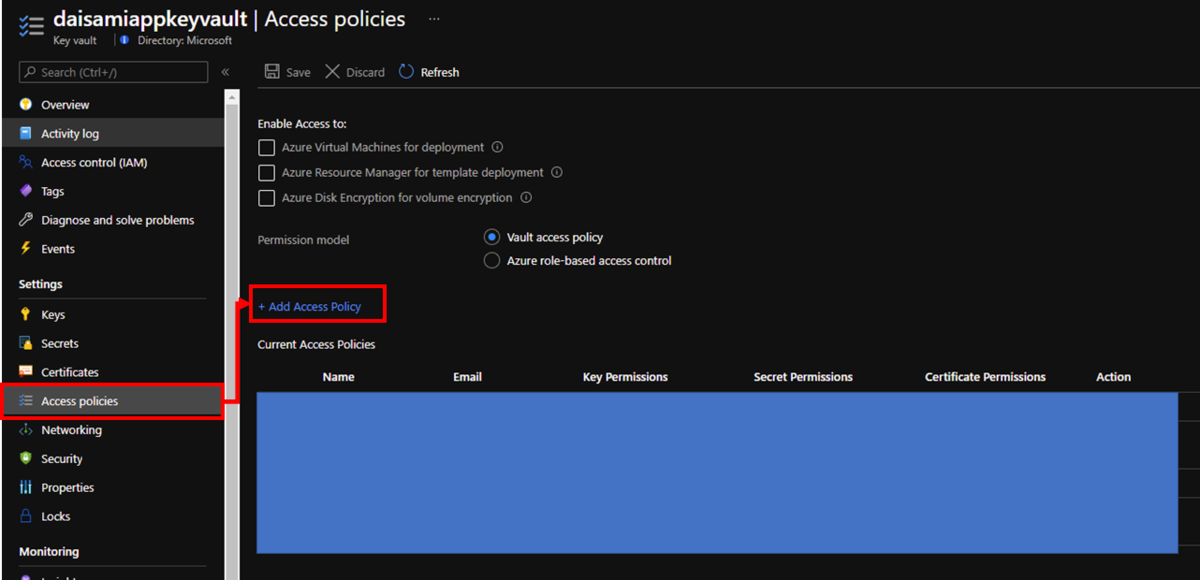
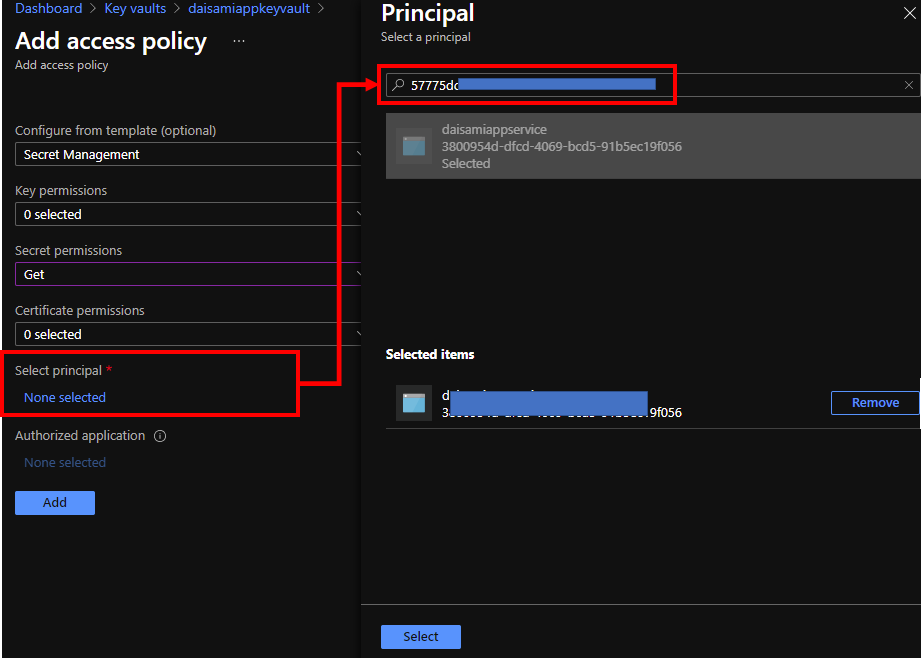
Select your managed identity by putting your object id on search box and choose it like below. Change Secret permissions as you need - I have changed only "Get" to allow only reading.
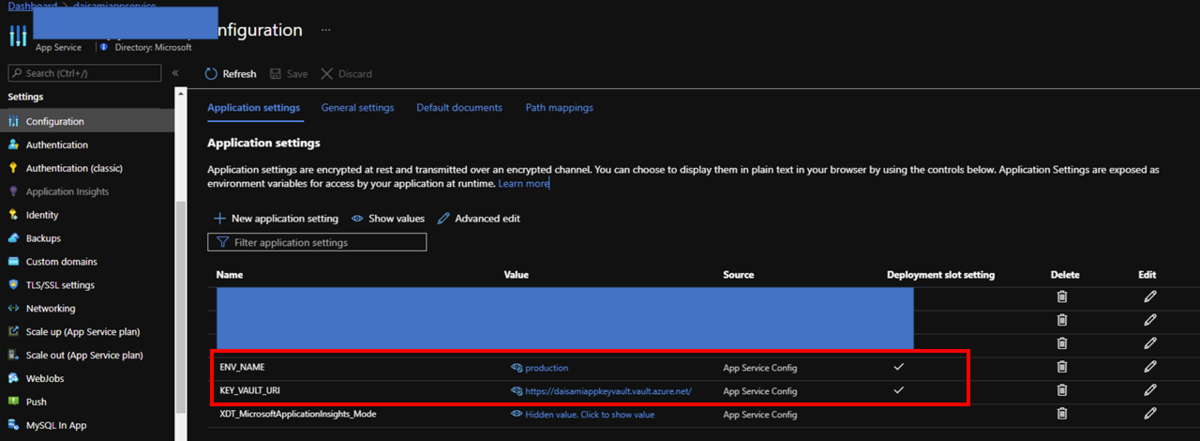
Visit your Azure App Service and put environment settings as KEY_VAULT_URI as https://xxxxxxxxxxxx.vault.azure.net/ and ENV_NAME as production like below.
Now, it's a time to write up your application code. Lunch your Visual Studio and import modules below, Azure.Identity and Azure.Security.KeyVault.Secrets, to utilize Managed Identity and Azure Key Vault.
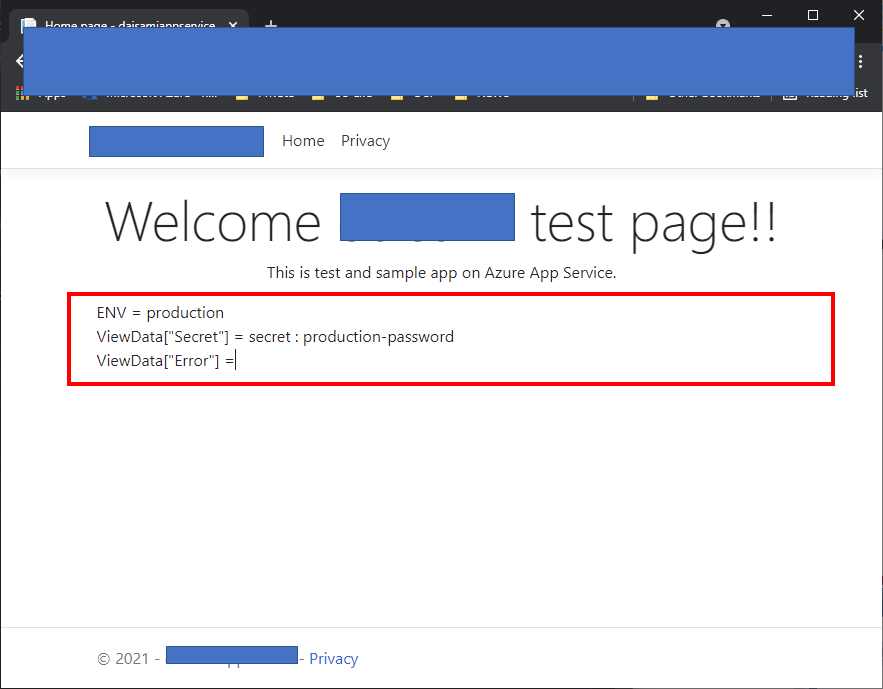
you can retrieve secret on your Key Vault from App Service.
using Azure; using Azure.Identity; using Azure.Security.KeyVault.Secrets; using Microsoft.AspNetCore.Mvc; using Microsoft.AspNetCore.Mvc.RazorPages; using Microsoft.Extensions.Logging; using System; using System.Collections.Generic; using System.Linq; using System.Threading.Tasks; namespace daisamiappservice.Pages { public class IndexModel : PageModel { private readonly ILogger<IndexModel> _logger; public IndexModel(ILogger<IndexModel> logger) { _logger = logger; } public async Task OnGet() { try { string uri = Environment.GetEnvironmentVariable("KEY_VAULT_URI"); SecretClient client = new SecretClient(new Uri(uri), new DefaultAzureCredential()); Response<KeyVaultSecret> secret = await client.GetSecretAsync("secret"); ViewData["Secret"] = $"{secret.Value.Name} : {secret.Value.Value}"; } catch (Exception exp) { ViewData["Error"] = $"Something went wrong: {exp.Message}"; } } } }
You can retrieve secret like here without putting any secret strings on your app.
Enable App Service deployment slot and Managed Identity to separate secrets completely for each environment
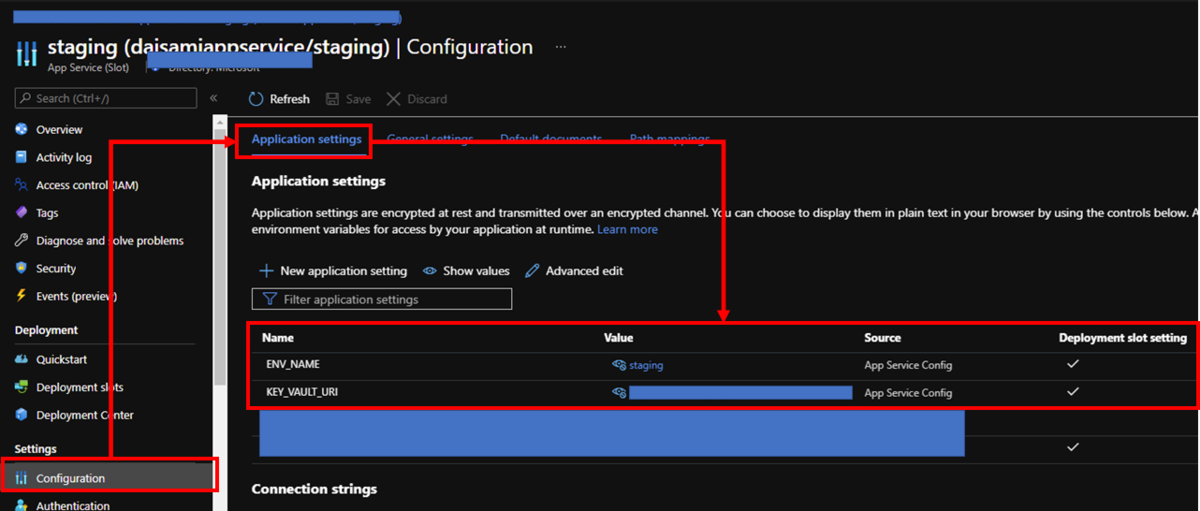
App Service offers deployment slots feature without lunching up new App Service instances. You just need to create deployment slot on your Azure App Service and enable managed identity again on your deployment slot because it's a separated Azure resource with production env. Create new Azure Key Vault and put settings like here. Don't forget to enable Deployment slot setting to prevent swap settings.
Now, you can deploy as single code for each environment. Deploy your app into deployment slot and swap it into production. You can confirm your settings like below.
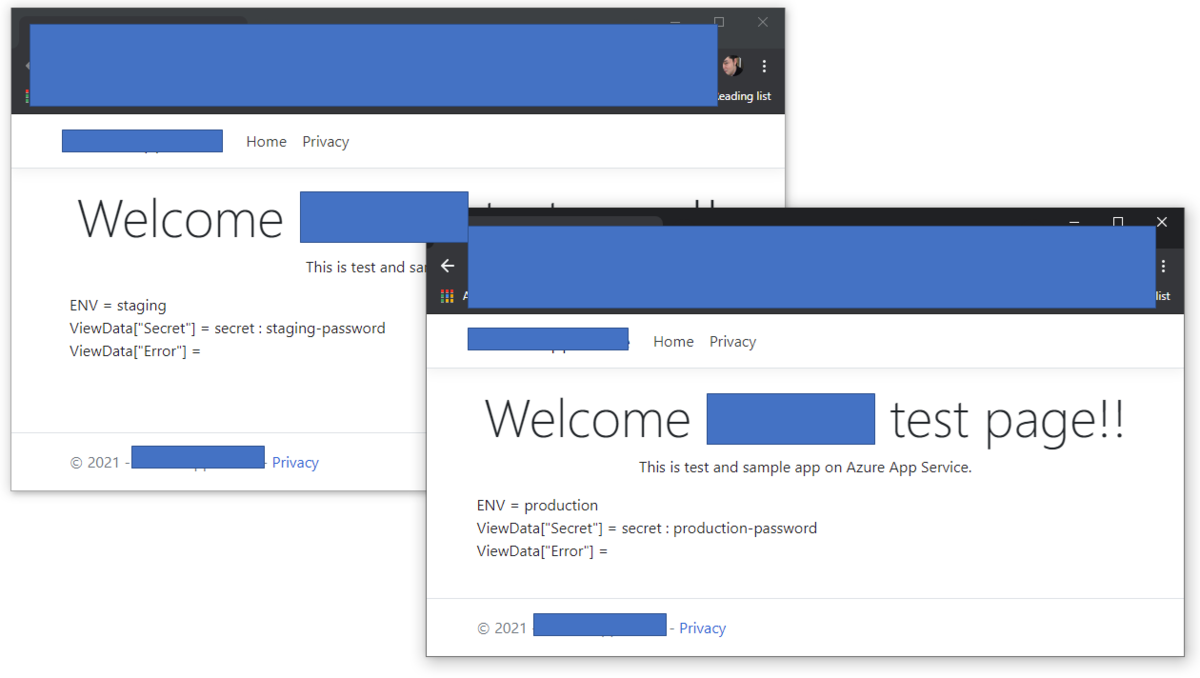
Finnally, you can store secrets within Azure Key Vault and retrieve them by using Managed Identity without any specific password on your application codes or settings.